SAML Integration Feature
Overview
The SAML (Security Assertion Markup Language) integration feature allows your SaaS application to authenticate users through external identity providers.
This enables tenants to use single sign-on (SSO) functionality and leverage their existing identity management systems.
Configuration Steps
The SaaSus Platform SAML integration feature can work with various SAML 2.0 compatible identity providers.
Here we explain the configuration steps using Microsoft Entra ID as a representative example of integration partners.
Even if you use other identity providers, the basic concepts and configuration items are common.
1. Obtain Entity ID/Reply URL
Execute the API to obtain Entity ID (identity_provider_configuration.entity_id) and Reply URL (identity_provider_configuration.reply_url)
https://docs.saasus.io/docs/reference/auth-api#tag/authInfo/operation/GetSignInSettings
{
"identity_provider_configuration": {
"domain": "xxxxxxxxxxxx.auth.ap-northeast-1.amazoncognito.com",
"entity_id": "urn:amazon:cognito:sp:ap-northeast-1_xxxxxxxxxxxx",
"redirect_url": "https://xxxxxxxxxxxx.auth.ap-northeast-1.amazoncognito.com/oauth2/idpresponse",
"reply_url": "https://xxxxxxxxxxxx.auth.ap-northeast-1.amazoncognito.com/saml2/idpresponse"
}
}
2. Microsoft Entra ID Configuration
Configure Microsoft Entra ID for SAML integration. Follow these steps:
-
Log in to Microsoft Entra ID
Microsoft Entra Admin Center -
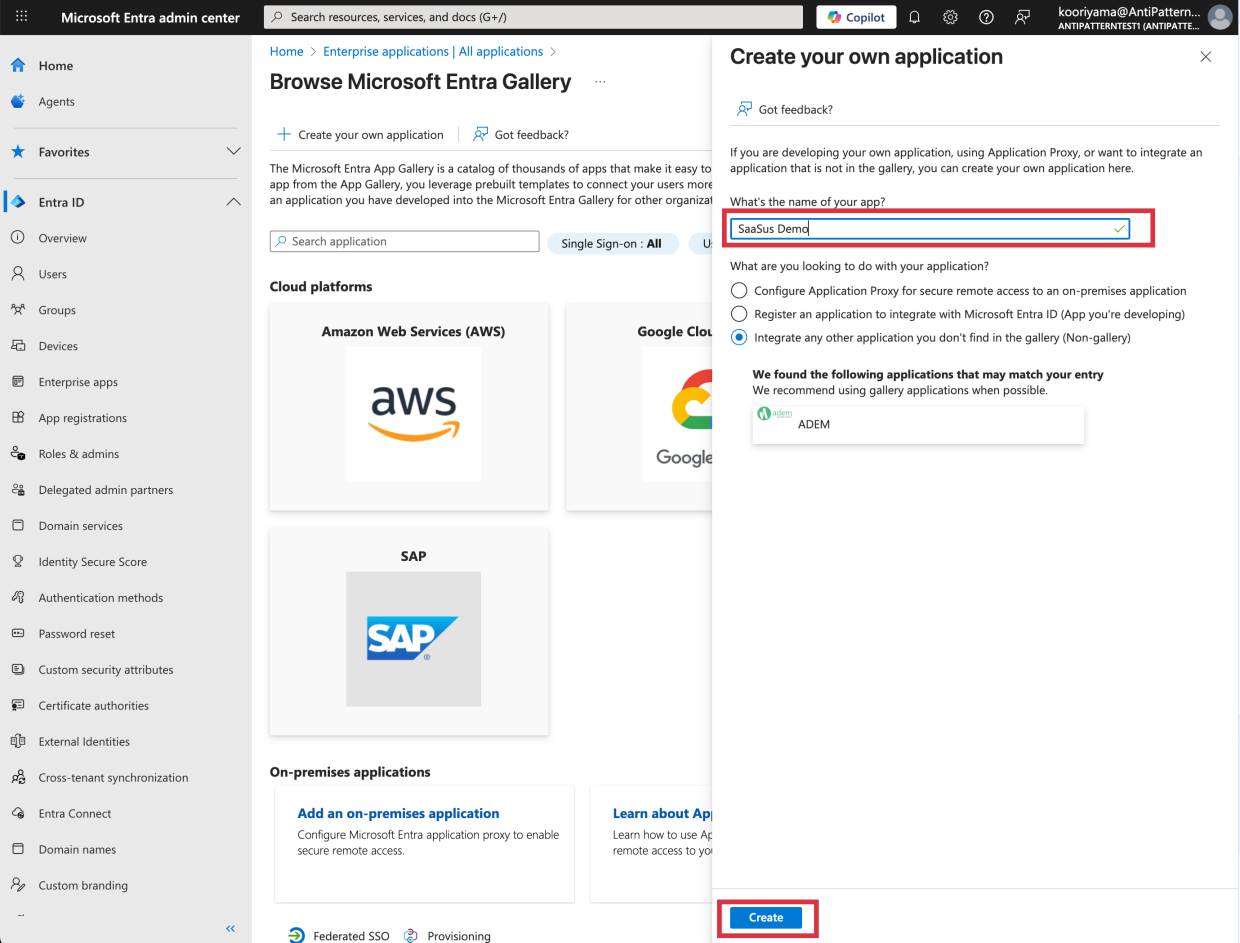
Create a new application
Go to Entra ID > Enterprise Apps and clickNew application

-
Set the application name and click
Create.
-
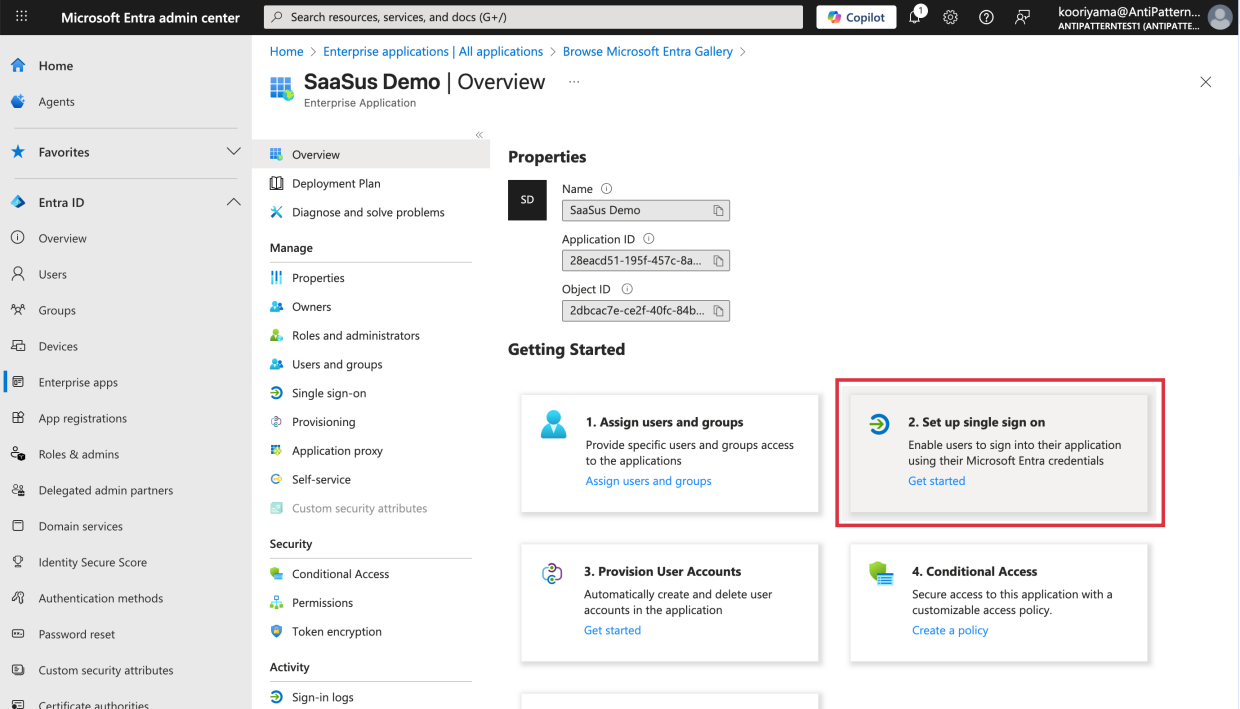
Select Single sign-on.
-
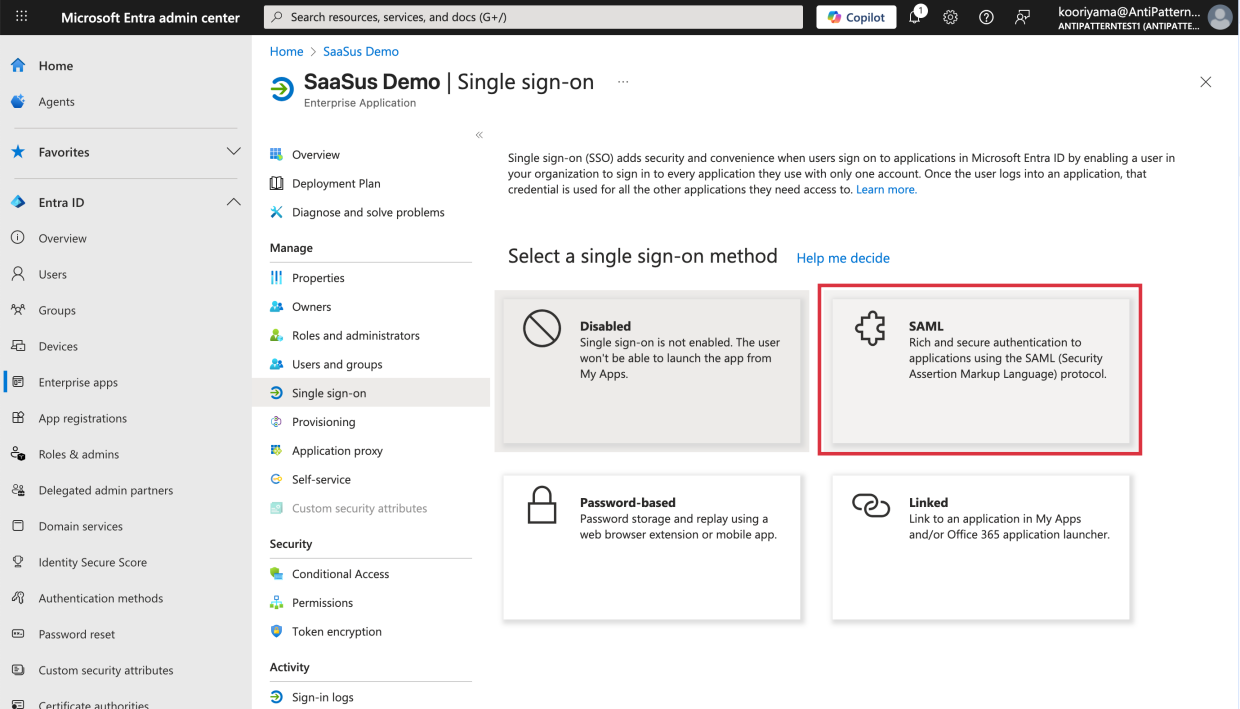
Select SAML.
-
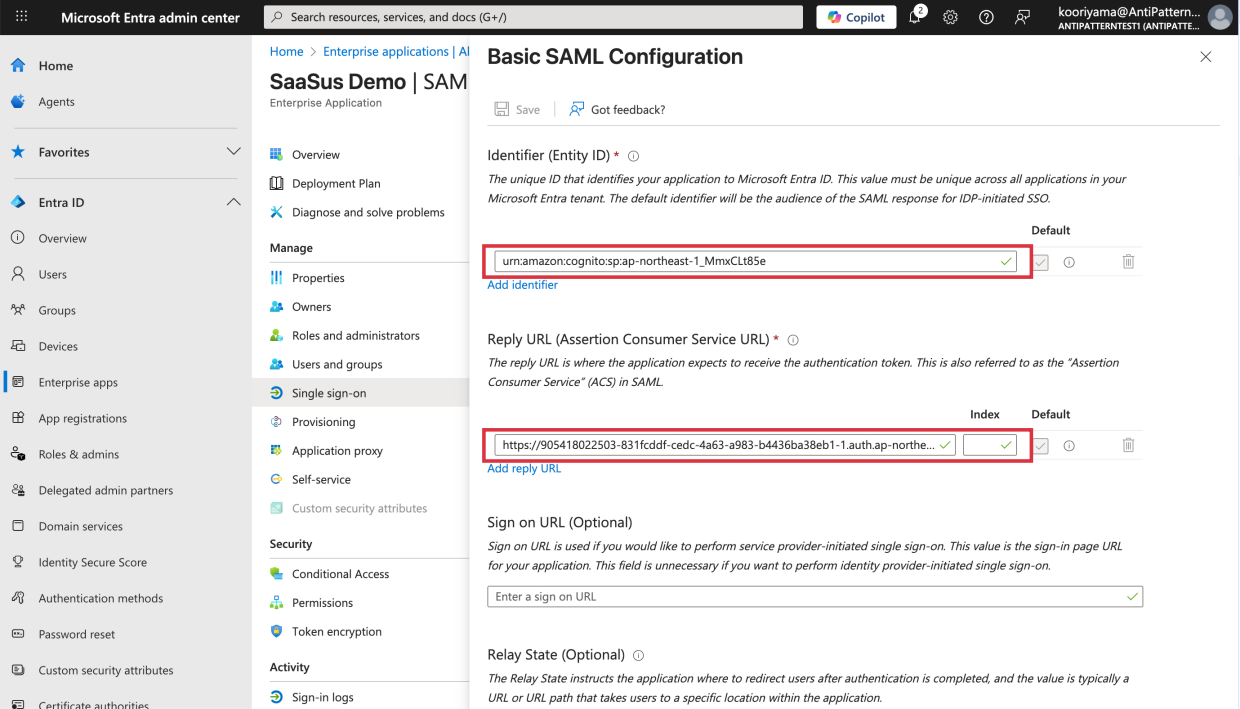
Edit Basic SAML Configuration and enter the following information
- Identifier (Entity ID): Enter the Entity ID obtained earlier.
- Reply URL: Enter the Reply URL obtained earlier.
-
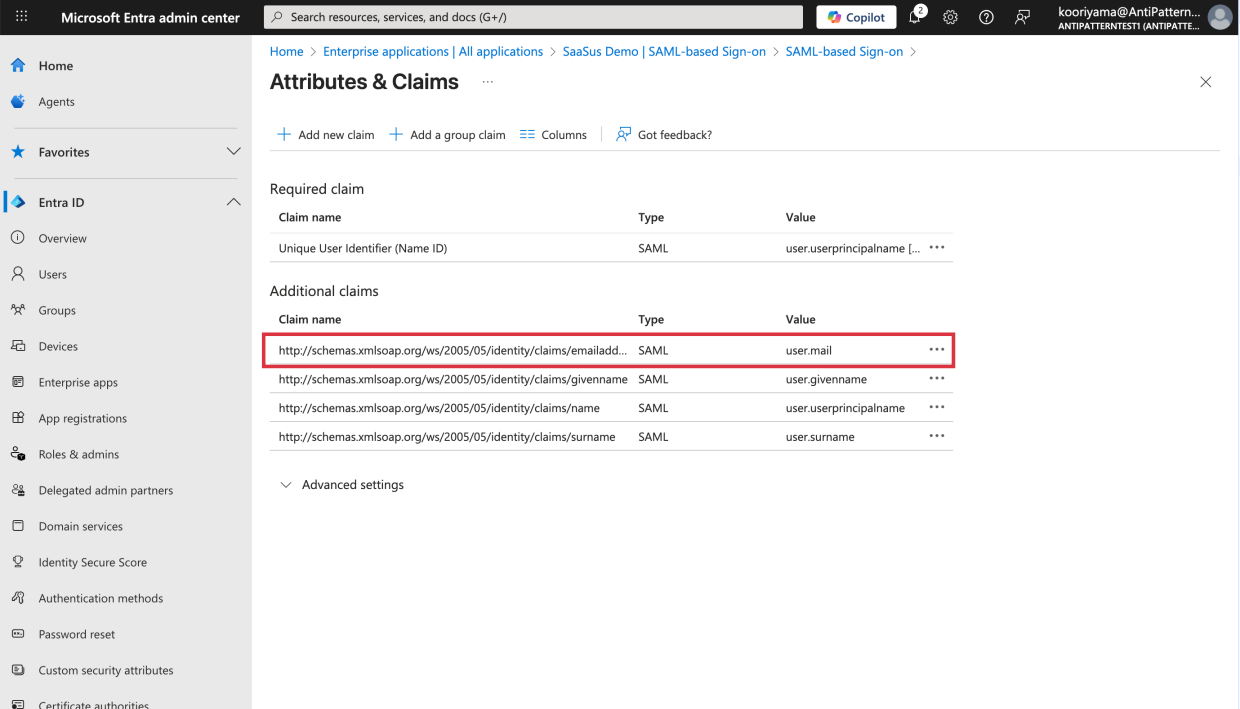
In Attributes & Claims settings, note the claim name set for
user.mail.
-
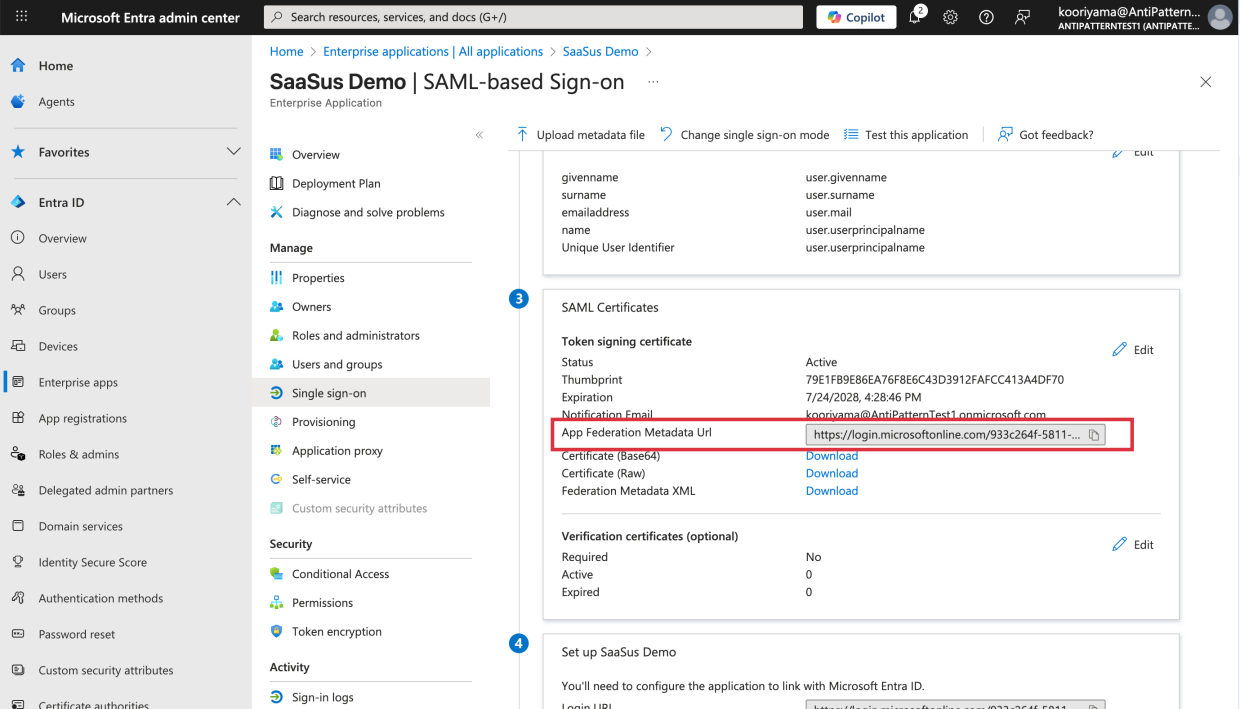
Note the
App Federation Metadata URLfrom the SAML Certificate section.
3. SaaSus Platform Configuration
Configure SAML integration using the SaaSus API.
Pass the following information to the API to set up SAML integration.
- provider_type: "SAML"
- metadata_url: App Federation Metadata URL from Microsoft Entra ID
- email_attribute: Claim name noted from Microsoft Entra ID (e.g.,
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress)
API: https://docs.saasus.io/docs/reference/auth-api#tag/tenant/operation/UpdateTenantIdentityProvider
{
"provider_type": "SAML",
"identity_provider_props": {
"metadata_url": "https://login.microsoftonline.com/xxxx-xxxx-xxxxx-xxxx-xxxx/federationmetadata/2007-06/federationmetadata.xml?appid=xxxx-xxxx-xxxxx-xxxx-xxxx",
"email_attribute": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"
}
}
4. Testing SAML Integration
-
Create login user in SaaSus
Create a user for the tenant that will use SAML integration from the SaaS operation console and assign roles.
The user's email address must match the email address set in Microsoft Entra ID. -
Verify sign_in_url
Use the SaaSus API to obtain the sign_in_url.
API: https://docs.saasus.io/docs/reference/auth-api#tag/tenant/operation/GetTenantIdentityProviders
{
"saml": {
"email_attribute": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress",
"metadata_url": "https://login.microsoftonline.com/xxxx-xxxx-xxxxx-xxxx-xxxx/federationmetadata/2007-06/federationmetadata.xml?appid=xxxx-xxxx-xxxxx-xxxx-xxxx",
"sign_in_url": "https://auth.implementation-sample2.sandbox.dev.saasus.io/sign-in/saml/6PcH3PYyte8ZTDZ65ul5jE"
}
}
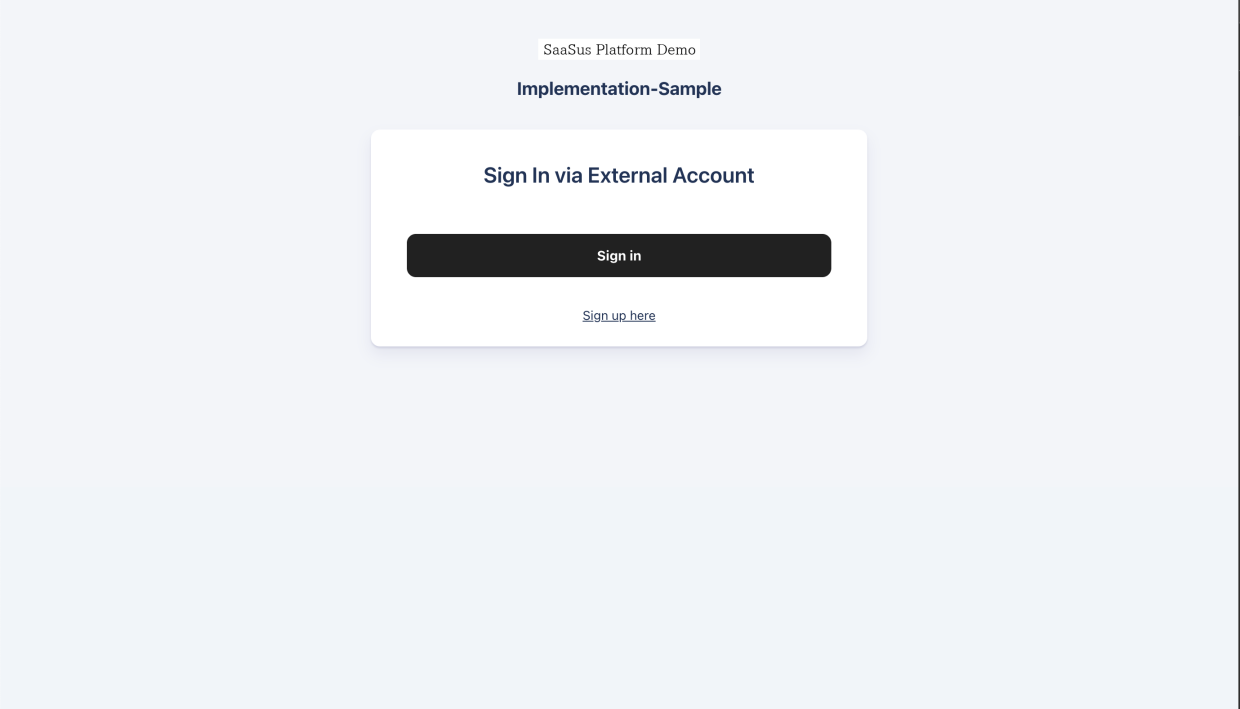
-
External account login screen
Access the obtained sign_in_url.
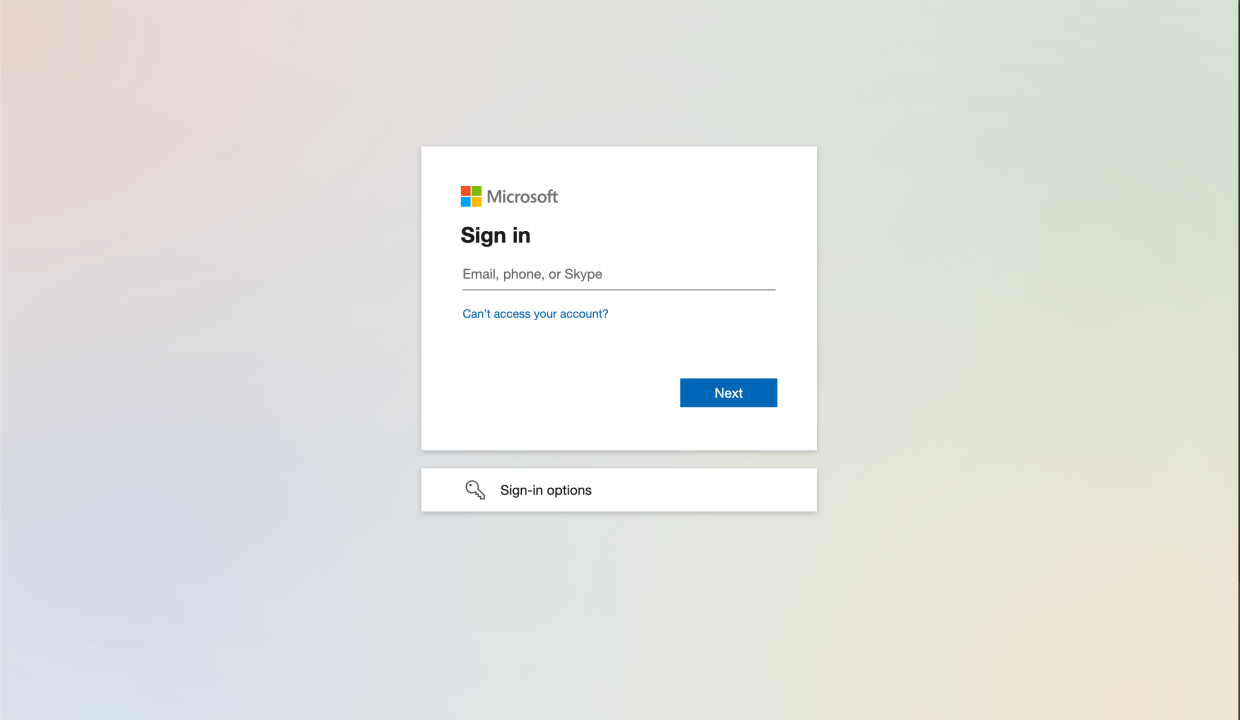
-
Login with Microsoft Entra ID
On the Microsoft Entra ID login screen, enter your username and password to log in.
Upon successful login, you will be redirected to the SaaS.
Notes
User Group Configuration
In Microsoft Entra ID, you can use the Users and Groups feature to assign users who will use SAML authentication to groups.
This allows you to control access so that only users belonging to specific groups can access the SaaS application.
From Microsoft Entra Admin Center > Enterprise Apps > Created Application > Users and Groups, assign users who will access SaaSus Platform to groups.